Exposing LabHost – Phishing as a Service Franchise – An OSINT Analysis
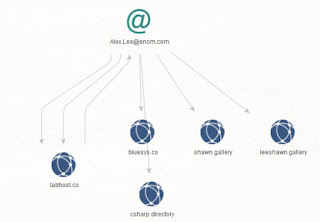
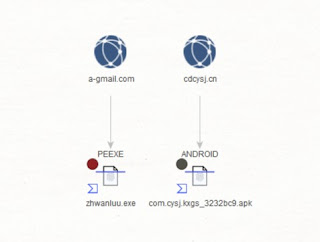
Dear blog readers, In this analysis I’ll provide actionable intelligence on the LabHost phishing as a service cybercrime enterprise. Sample URLs known to have been involved in the campaign include: hxxp://labhost[.]cc hxxp://labhost[.]co hxxp://labhost[.]xyz – Email: zztopd[.]rambler.ru hxxp://labhost[.]ru hxxp://lab-host[.]ru Related domains known to have been registered using zztopd@rambler.ru: hxxp://russiancloud[.]xyz hxxp://onelab[.]xyz hxxp://onebio[.]xyz hxxp://inforussia[.]xyz hxxp://labservice[.]xyz hxxp://labcentral[.]xyz hxxp://gorussian[.]xyz hxxp://ecoserver[.]xyzRead More